Case Study:
Project Challenge
Project description
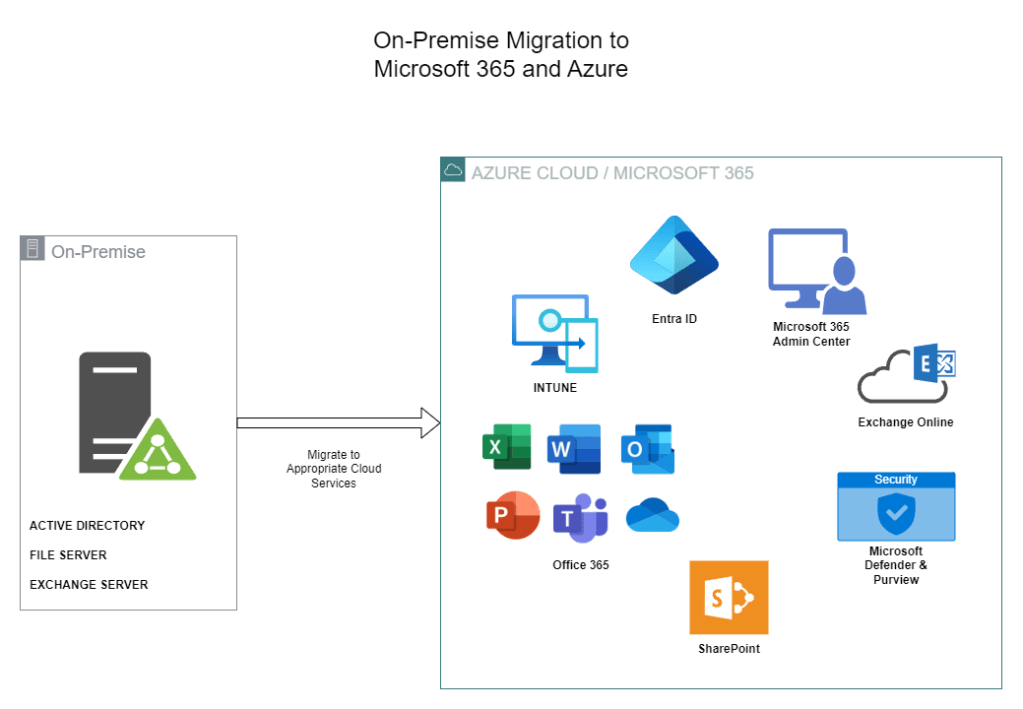
The project addressed the evolving needs of the client’s digital infrastructure, which presented several challenges. Initially, the client operated with existing users on-premise, including on-prem Exchange and File Server.
Key challenges included optimizing Active Directory, configuring Microsoft 365 Admin Center, enhancing Exchange Online, and ensuring seamless integration of Teams, SharePoint, and Intune. Additionally, the project required the implementation of robust security measures, such as multi-factor authentication, conditional access policies, and threat detection, to safeguard against potential cyber threats.
Technology
Public Cloud
Timeline
4 Months
Role
Cloud Architect
Date Completed
December 2023
Project Solution
To overcome these challenges, a structured approach was adopted, focusing on specific milestones within each component of the project. It was decided that the File server could be replaced with a cloud-based storage solution and the exchange server could be retired for an Exchange online.
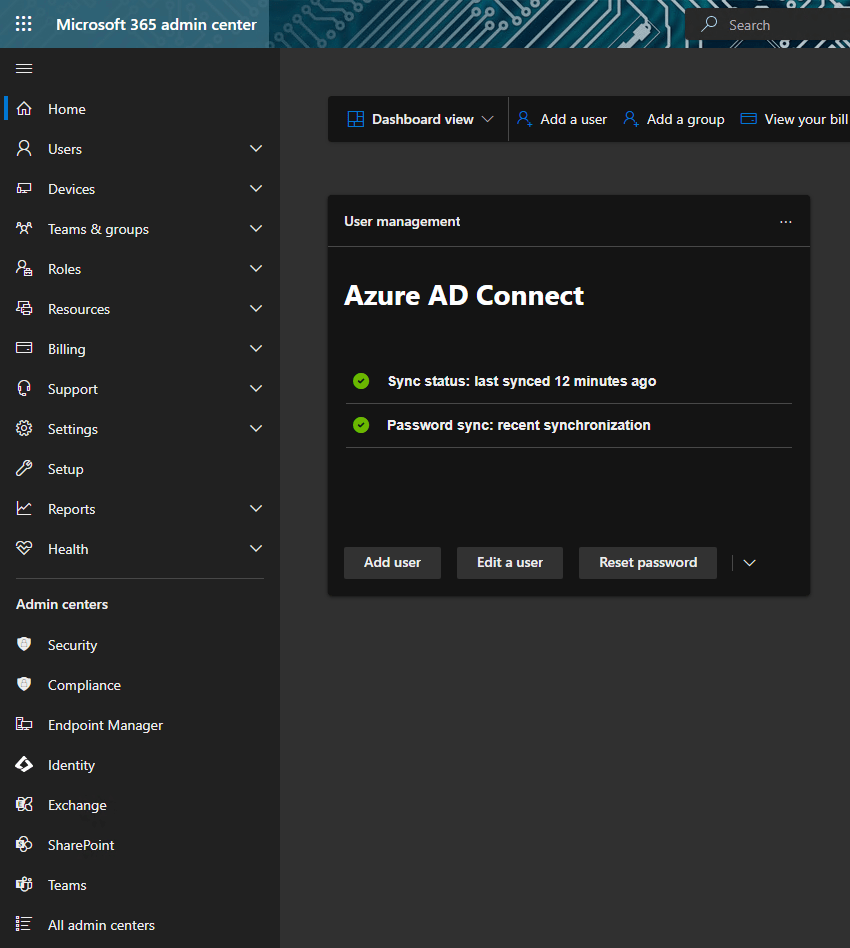
Since the AD server was relatively up to date we utilized Entra Connect (Azure AD Connect / DirSync), security best practices were implemented for AD Connect service accounts, facilitating the seamless integration of on-premise users with the cloud environment.
For the Microsoft 365 Admin Center, meticulous setup including domain configuration, group allocation, user addition, and license recommendation was undertaken, while also documenting a streamlined onboarding process for new users.
Email management underwent thorough enhancement, including mailbox permissions assignment, forwarding rules implementation, messaging rule setup, and mailbox archives configuration for pertinent users.
Enterprise application centering on user needs was meticulously addressed through license recommendation, multi-factor authentication setup via conditional access policies, enterprise/app application configuration, and management-centric access reviews.
Team and SharePoint environments were tailored to meet organizational requirements, including the setup of team groups, policy formulation, data migration, and appropriate access controls.
Device management and security were prioritized, encompassing device enrollment, compliance policies establishment, and license setup to fortify organizational defenses.
Microsoft Defender received comprehensive attention, with the setup of threat and alert policies, message quarantine review, and documentation for report generation, all aimed at bolstering the security posture and achieving higher secure scores.
Governance policies were instituted to govern Microsoft 365 environments effectively, alongside procedures documented for eDiscovery case generation, ensuring streamlined operations and compliance adherence.
The transition from on-premise to cloud not only streamlined processes but also fortified security measures. This comprehensive approach to cloud migration resulted in tangible improvements for my client, solidifying their digital infrastructure for future growth and efficiency.
Security Enhancements
A critical focus of the project was improving the organization’s overall security posture throughout the migration process. The following measures were implemented to enhance security:
Active Directory (AD) and Azure AD Integration:
- Secured the Azure AD Connect setup by adhering to best practices, including using minimal-privilege service accounts and enabling password hash synchronization for enhanced resilience.
- Enabled Conditional Access Policies to control access to cloud resources based on user location, device compliance, and sign-in risk.
Microsoft 365 Email Security:
- Configured anti-phishing filters and safe links policies to protect users from malicious emails and links.
- Implemented multi-factor authentication (MFA) for all users to secure account access against unauthorized logins.
- Deployed spam and malware filtering rules to block harmful emails at the perimeter.
- Enabled email encryption for sensitive communications.
Enterprise Application Security:
- Configured application permissions based on the principle of least privilege to minimize exposure of critical data.
- Regularly conducted access reviews to ensure only authorized users retained access to enterprise applications.
SharePoint and Teams Security:
- Applied access control policies to restrict sensitive data access to authorized personnel only.
- Monitored and configured sharing permissions to prevent inadvertent external data exposure.
- Deployed data loss prevention (DLP) policies to safeguard sensitive data within Teams and SharePoint.
Device Management and Compliance:
- Enforced compliance policies requiring secure configurations for all enrolled devices.
- Enabled BitLocker encryption and remote wipe capabilities to protect data in the event of device loss or theft.
- Ensured all devices were updated with the latest security patches.
Microsoft Defender Enhancements:
- Configured threat detection policies to identify and respond to suspicious activities quickly.
- Enabled automated investigations and response (AIR) features to remediate threats with minimal manual intervention.
- Conducted regular reviews of message quarantine logs and established reporting protocols to ensure proactive threat management.
Governance and Compliance:
- Defined and implemented governance policies to manage data access and lifecycle effectively.
- Set up eDiscovery cases to ensure compliance with regulatory requirements and enable efficient incident investigations.
- Created audit trails for all critical administrative actions to enhance transparency and accountability.
These enhancements significantly increased the organization’s Microsoft Secure Score, reducing vulnerabilities and improving their readiness to detect, prevent, and respond to security threats. This proactive approach not only fortified the client’s digital ecosystem but also ensured alignment with industry best practices for cybersecurity.
